






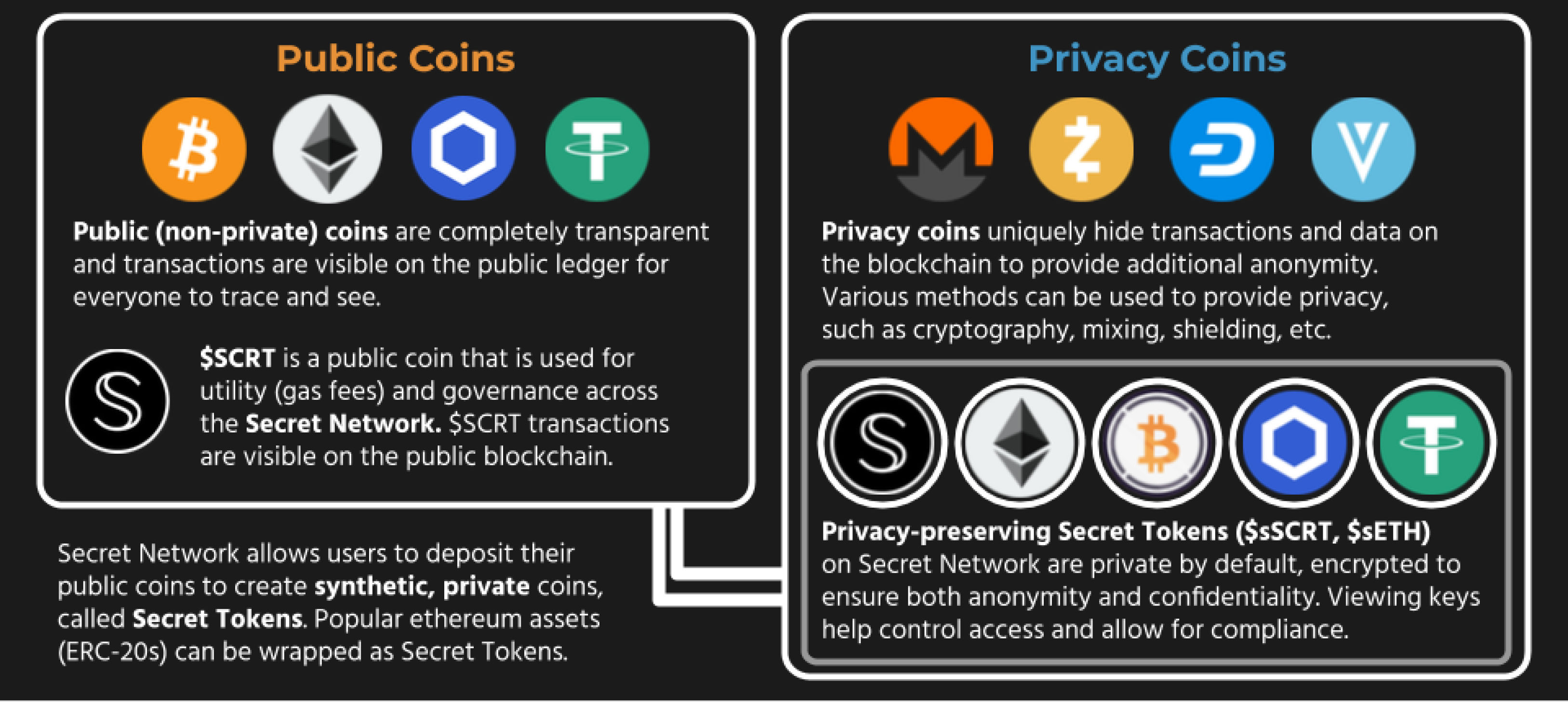
Secret Tokens are a powerful concept - they’re programmable like ERC-20s and usable in applications, but they remain private-by-default like Monero and similar coins. They can represent off-chain assets, or they can be fully native to Secret Network. Anyone can create a token, which can then be transferred between wallets and used in smart contracts.
When interacting with Secret Tokens, all transactions (including the recipient and the amount transferred) and rolling balances are kept encrypted, ensuring both anonymity and confidentiality. Individuals must generate a “viewing key” in order to reveal these values, and can choose to share this with third parties for compliance situations.
It should be noted that minting and burning Secret Tokens are public transactions and could be observed on-chain. For example, the minting of sSCRT will require SCRT which is a public token.
SNIP-20, is a specification for private fungible tokens based on CosmWasm on the Secret Network. The name and design is loosely based on Ethereum’s ERC-20 & ERC-777 standards, and a superset of CosmWasm’s CW-20. Key additions to this spec over the CW-20 specification are mostly for privacy focused features, and as such will strive to maintain compatibility.
Secret Network’s vision is to create an environment with privacy-by-default. This means that individuals should have control of the level of privacy as opposed to complete transparency or complete privacy. This is also critical to build a compliant financial ecosystem.
“Viewing Keys” are used to validate the identity of someone who queries a specific account. They can be generated to allow third parties, including other contracts, to view an individual’s balance. These will be particularly important in the current environment to enable individuals to provide relevant data to auditors, wallets and explorers when users opt-in to share this information.
There are already a number of uses for Secret Tokens within the Secret Network ecosystem. These include:
There are many more products being developed which will further utilize the potential of Secret Tokens for DeFi, NFTs and beyond.
Secret Bridges connect Secret Network with other blockchain networks to allow holders from various ecosystems to create privacy-preserving versions of their asset, called Secret Tokens. Secret Tokens are a powerful concept - they’re programmable like ERC-20s and usable in applications, but they remain private by default like Monero and similar coins. Once assets cross the Secret Bridge as Secret Tokens, they can be used across Secret DeFi applications which are natively private by default and are multichain interoperable, meaning they support assets across various blockchain ecosystems.
Secret already allows a number of tokens across Ethereum and Binance Smart Chain to be moved and swapped privately across chains. New bridges will give the same access and functionality to other blockchain networks.
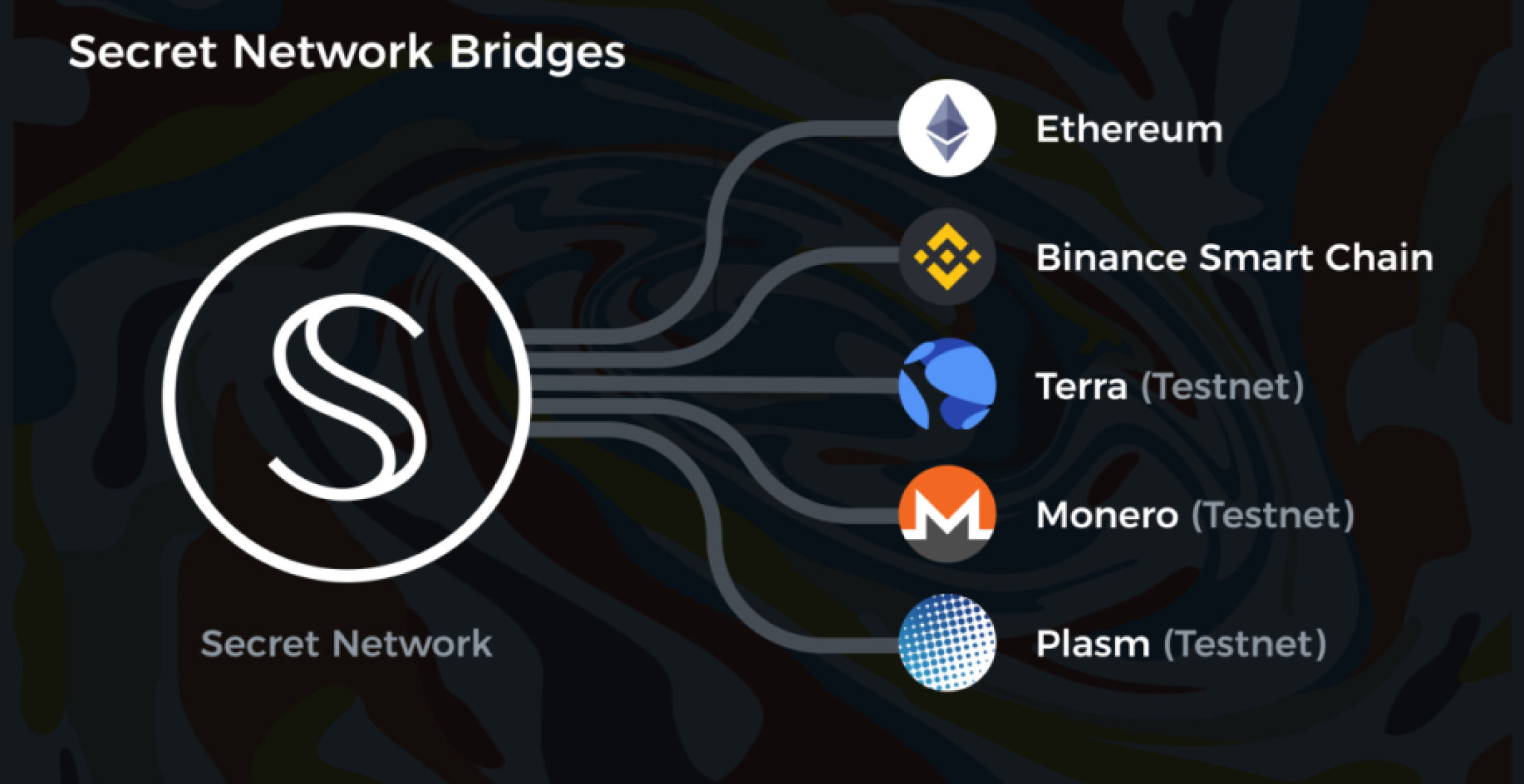
Secret Bridges utilizes a 3 of 5 multisig authorisation process. This means that 3 out of 5 parties trusted with operating the bridge are required to approve a transaction across the bridge. These bridge operators are very reputable staking operators - Figment, Staked, B-Harvest, Citadel.one and Enigma.
Bridge operators are responsible for watching the chain for new events. Once a new event is found, one of the bridge operators proposes a transaction, which is then confirmed by other operators. The multisig authorisation process makes it significantly more difficult for the Secret Bridge to be compromised by removing the single point of failure associated with having a single approver.
Secret Network’s mission is to become the go-to multichain interoperable privacy hub. This vision of the future involves many different blockchains with specific purposes, all of which benefit from being able to use private data safely and securely. Secret Network is already providing access to programmable privacy to multiple blockchain networks. As new Secret Bridges are developed, Secret Network will continue to expand and further solidify its footprint as the privacy hub for all blockchains.

If you are interested in building bridges between Secret Network and other blockchains, come join our developer community! Our team is already working with a number of developers to build new Secret Bridges across various ecosystems, and we would love to collaborate and share resources with you.
By building bridges, you can make programmable privacy possible for new blockchain networks and help Secret Network expand its footprint as the multichain privacy hub for all blockchains.



© Secret Network. All Rights Reserved.